How to View RDP Connection Logs in Windows
In this article we will take a look at the features of Remote Desktop Protocol (RDP) connection auditing and log analysis in Windows. Typically, it is useful when investigating various incidents on Windows servers when a system administrator is required to provide information about what users logged on to the server, when he logged on and off, and from which device (name or IP address) the RDP user was connecting.
Remote Desktop Connection Events
Like other events, the Windows RDP connection logs are stored in the event logs. The Windows logs contain a lot of information, but it can be difficult to find the right event quickly. When a user remotely connects to a Windows server, many events are generated in the Windows logs. We will take a look at the following:
- Network Connection
- Authentication
- Logon
- Session Disconnect/Reconnect
- Logoff
Network Connection Events
Network Connection connects user’s RDP client with the Windows server. That logs EventID – 1149 (Remote Desktop Services: User authentication succeeded). The presence of this event does not indicate successful user authentication. This log can be found at Applications and Services Logs ⇒ Microsoft ⇒ Windows ⇒ Terminal-Services-RemoteConnectionManager ⇒ Operational. You can filter this log by right clicking on Operational log ⇒ Selecting “Filter Current Log” and type in EventID 1149.

The result is a list with the history of all network RDP connections to this server. As you can see, the log file contains the username, domain (When Network Level Authentication (NLA) authentication is used), and IP address of the computer from which the RDP connection is made.

Authentication Events
User authentication can be successful or unsuccessful on the server. Navigate to Windows logs ⇒ Security. We are interested in logs with EventID – 4624 (An account was successfully logged on) or 4625 (An account failed to log on). Pay attention to the LogonType value in the event. LogonType – 10 or 3 indicates a new logon to the system. If LogonType is 7, it indicates re-connection to an existing RDP session.

The username of the connecting account is written in the Account Name field, his computer name is written in Workstation Name, and the IP address in Source Network Address.
Take a look at TargetLogonID field, which is a unique user session identifier that can be used to track further activity of this user. However, if a user disconnects from the RDP session and reconnects to the session again, the user will be issued a new TargetLogonID (although the RDP session remains the same).
You can get a list of successful authentication events over RDP (EventID 4624) using the following PowerShell command:
Get-EventLog security -after (Get-date -hour 0 -minute 0 -second 0) | ?{$_.eventid -eq 4624 -and $_.Message -match 'logon type:\s+(10)\s'} | Out-GridView
Logon Events
RDP logon is the event that appears after successful user authentication. Log entry with EventID – 21 (Remote Desktop Services: Session logon succeeded). This log can be found in Applications and Services Logs ⇒ Microsoft ⇒ Windows ⇒ TerminalServices-LocalSessionManager ⇒ Operational. As you can see here you can see the RDP Session ID for the user.

“Remote Desktop Services: Shell start received” details in EventID 21 means that the Explorer shell has been successfully launched in the RDP session.
Session Disconnect and Reconnect Events
Session Disconnect/Reconnect events have different codes depending on what caused the user to end the session, for example disable by inactivity, selecting “Disconnect” in Start menu, RDP session drop by another user or administrator, etc. These events can be found in Applications and Services Logs ⇒ Microsoft ⇒ Windows ⇒ TerminalServices-LocalSessionManager ⇒ Operational. Let’s take a look at the RDP events that may be of interest:
- EventID – 24 (Remote Desktop Services: Session has been disconnected) – the user has disconnected from the RDP session.
- EventID – 25 (Remote Desktop Services: Session reconnection succeeded) – The user has reconnected to his existing RDP session on the server.
- EventID – 39 (Session A has been disconnected by session B) – user disconnected from his RDP session by selecting the appropriate menu item (not just closed the RDP client window by clicking on “x” in the top right corner). If the session IDs are different, then the user has been disconnected by another user or administrator.
- EventID – 40 (Session A has been disconnected, reason code B). Here you should look at the reason code for the disconnection in the event. For example:
- Reason code 0 (No additional information is available) – usually indicates that the user just closed the RDP client window.
- Reason code 5 (The client’s connection was replaced by another connection) – the user re-connected to his old session.
- Reason code 11 (User activity has the disconnect) – the user clicked the Disconnect button on the menu.
- EventID – 4778 in Windows log ⇒ Security (A session was reconnected to a Window Station). The user re-connected to an RDP session (the user is given a new LogonID).
- EventID 4799 in Windows Logon ⇒ Security (A session was reconnected to a Window Station). Disconnection from an RDP session.
Logoff Events
Logoff logs track the user disconnection from the system. In the Applications and Services Logs ⇒ Microsoft ⇒ Windows ⇒ TerminalServices-LocalSessionManager ⇒ Operational logs we can find EventID 23. In this case in Security log we need to search for EventID 4634 (An account was logged off).
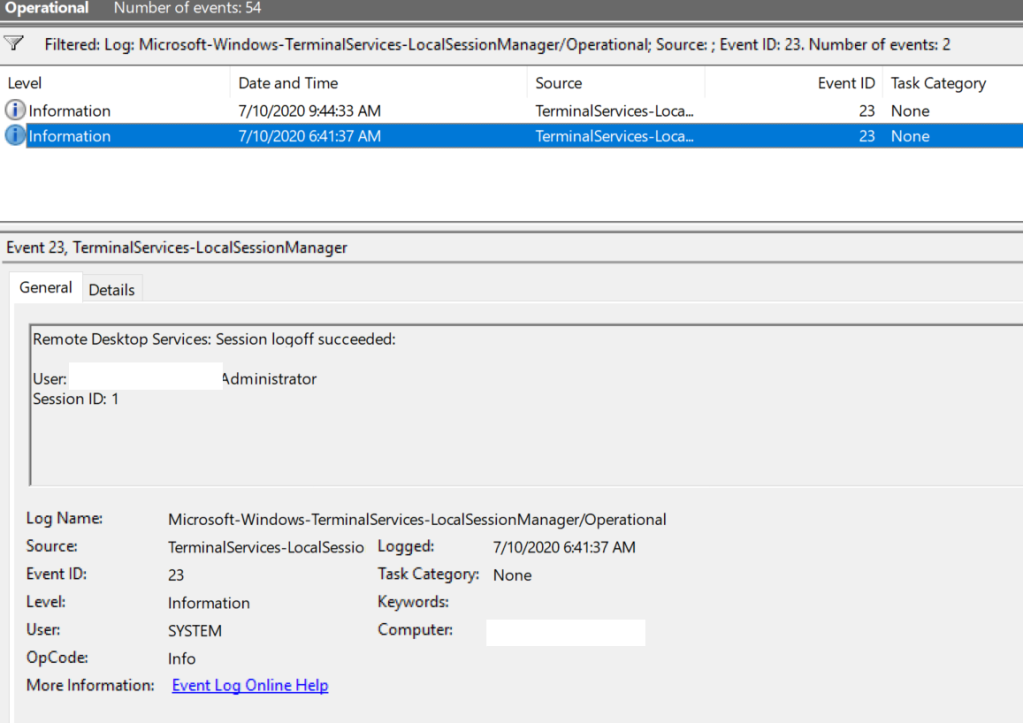
Event 9009 (The Desktop Window Manager has exited with code (x)) in the System log shows that the user initiated the end of the RDP session and the user’s window and graphical shell were terminated. Below is a small PowerShell that uploads the history of all RDP connections for the current day from the Remote Desktop Service server. The table below shows the connection time, client IP address, and RDP username (you can include other logon types in the report if necessary).
Get-EventLog -LogName Security -after (Get-date -hour 0 -minute 0 -second 0)| ?{(4624,4778) -contains $_.EventID -and $_.Message -match 'logon type:\s+(10)\s'}| %{
(new-object -Type PSObject -Property @{
TimeGenerated = $_.TimeGenerated
ClientIP = $_.Message -replace '(?smi).*Source Network Address:\s+([^\s]+)\s+.*','$1'
UserName = $_.Message -replace '(?smi).*Account Name:\s+([^\s]+)\s+.*','$1'
UserDomain = $_.Message -replace '(?smi).*Account Domain:\s+([^\s]+)\s+.*','$1'
LogonType = $_.Message -replace '(?smi).*Logon Type:\s+([^\s]+)\s+.*','$1'
})
} | sort TimeGenerated -Descending | Select TimeGenerated, ClientIP `
, @{N='Username';E={'{0}\{1}' -f $_.UserDomain,$_.UserName}} `
, @{N='LogType';E={
switch ($_.LogonType) {
2 {'Interactive - local logon'}
3 {'Network conection to shared folder)'}
4 {'Batch'}
5 {'Service'}
7 {'Unlock (after screensaver)'}
8 {'NetworkCleartext'}
9 {'NewCredentials (local impersonation process under existing connection)'}
10 {'RDP'}
11 {'CachedInteractive'}
default {"LogType Not Recognised: $($_.LogonType)"}
}
}}
Exporting RDP logs
Sometimes it is needed to export RDP logs into Excel table, in this case you can upload any Windows log to a text file and afterwards import it into Excel. You can export the log from the Event Viewer console or from the command line:
WEVTUtil query-events Security > c:\ps\security_log.txt
Or:
get-winevent -logname "Microsoft-Windows-TerminalServices-LocalSessionManager/Operational" | Export-Csv c:\ps\rdp-log.txt -Encoding UTF8
A list of the current RDP sessions on the server can be displayed as a command “Qwinsta”

The command returns as session identifier, username and status (Active/Disconnect). This command is useful when you need to determine the RDP session ID of a user during a shadow connection.
After defining a Session ID you can list running processes in a particular RDP session:
qprocess /id:1

So here are the most common ways to view RDP connection logs in Windows.



This is pretty handy. Thanks for sharing!
LikeLiked by 1 person
Maybe credit the source? http://woshub.com/rdp-connection-logs-forensics-windows/
LikeLike
Very good article. Thanks.
What about the client side? Are there any logs?
LikeLike
Do you have to have logging enabled somewhere? When we look a the connection events, the workstation name and IP are blank.
LikeLike